Authentication is the act of providing assertion, such as the identity of a computer system user.
In simpler terms, authentication is the process of determining whether a user is in fact who they claim to be. This process has evolved through the ages making it foolproof and concrete.
What did we use prior to cryptographic authentication model?
Prior to the modern authentication processes, fingerprints were considered to be the most authoritative method of authentication until it was realized that fingerprints were also vulnerable to spoofing.
In fact, Fingerprint spoofing was the prevalent method of bio metric spoofing in parts of the US and Europe in the late 2000s.
This situation has led to a change in perspective regarding fingerprints.
Hence, digital authentication was developed to ensure that a robust methodology exists to authenticate an individual.
In the modern authentication model, an account (be it an individual or corporate) is authenticated using a unique identifier and a secret identifier.
The unique identifier is always either a password or mail address but sometimes both. On the other hand, the secret identifier is mostly a password or an OTP (One time password).
Why was authentication required in the first place?
In the midst of the dot.com bubble (internet boom), major services including banking, stock trading, research, social networking, enterprise utilities were migrated to the internet.
This enabled better accessibility, cost efficiency and convenience to the global consumers which includes both enterprises and individual users.
It also introduced a new concern, which is the privacy and security of the hosted data.
For instance, a banking service on the web would have users of different roles having various access and power.
- Customers (Minimal access)
- Administrator (Administrative access)
- Bank employees (Internal access)
Though, customers are the target and primary users of the services, they should not have access to data that they do not require.
An individual should be able to view her/his personal information like
- Bank balance
- Account limit
- Outstanding amount
- Periodical summary
What is not the concern of an individual is sensitive information about the operating bank like
- Banking model
- Other account details
- Bank database
- Profit margin
Similarly, an administrator has their own set of well-defined access rules, although more access than that of an individual user which includes,
- View transaction history of users
- View user reports
- Block/Unblock suspicious accounts
- Mark accounts for suspicious activity
but still has restrictions as the user does, an administration cannot view the banking company’s sensitive details.
The only category of user which has access to some (if not all) insight of the company is the employee’s account.
The above segregation of access rules is achieved through a related process called authorization, which controls what the authenticated account has access to.
So, authenticating the account’s role is very crucial only after which authorization can be done, so that we can ensure scenarios like the below can be avoided.
Individual trying to login with employee’s identity.
Websites like Yahoo, Equifax, and Adobe have fallen victim to data breaches in the past and are prime examples of what happens when organizations fail to secure their websites. Use these companies as a warning to demonstrate the negative consequences of insecure user authentication processes. Not only were these scenarios costly to the organizations involved, but it also led to damaged reputations and decreased user trust.
That’s why it’s so important that your organization is not the next on that list of victims. In order to prevent such a situation, it’s a good idea to invest in high-quality authentication tools to help you secure your website and protect it from potential breaches.
This is exactly where cryptography came to the rescue, as the conventional signature method proved to be spoof prone. Traditional signatures were replaced with cryptographic signatures. Cryptographic signatures also ensured data integrity making use of public/private keys mechanism.
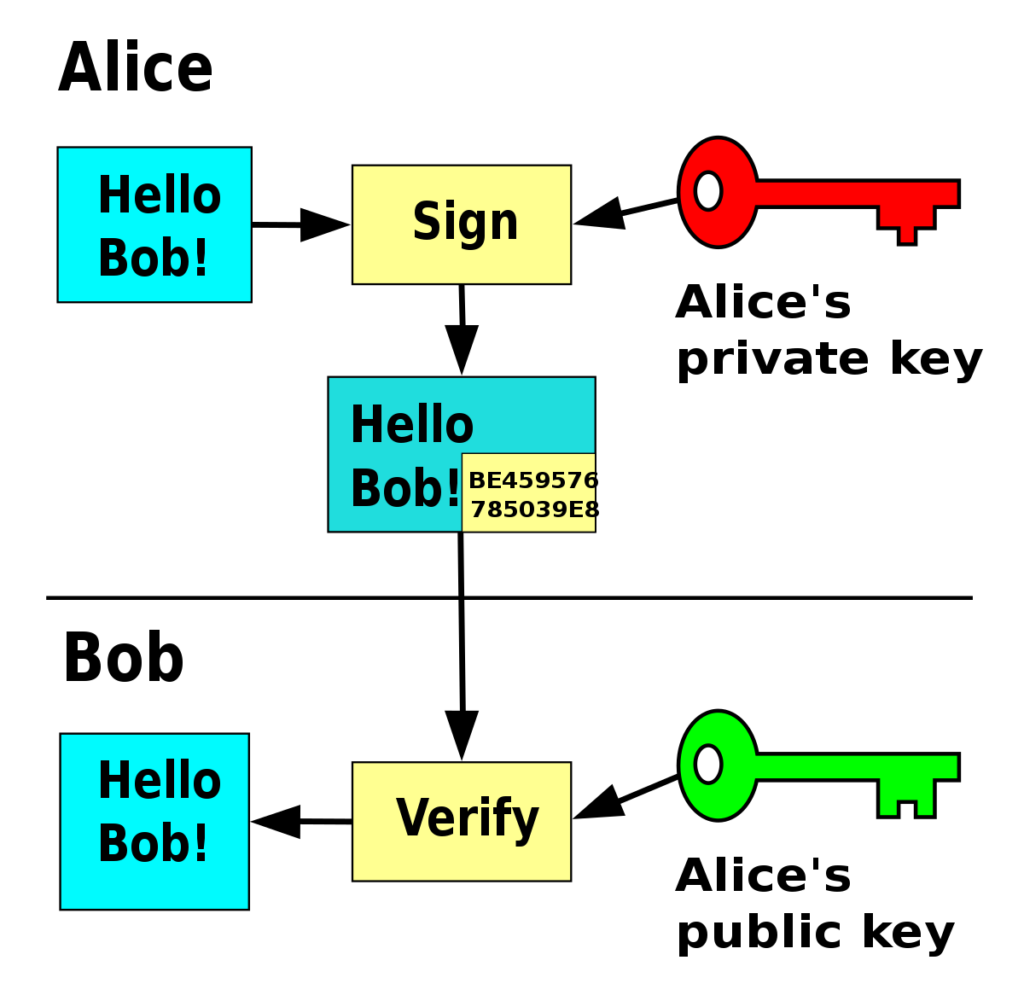
Other cryptographic components such as hashing, encryption/decryption make data theft/impersonation impossible.
Let us now understand how authentication actually works.
The process of authentication starts when the user provides information to the website, that is sufficient to prove their claimed identity.
Authentication service on the server side of the web application is responsible to verify the user’s identity and provide him access.
There are three primary tasks involved in the process of authentication,
- Users provide their credentials
- Server verifies the provided credentials
- Approve (or decline) the request
There would two main components in the process of authentication,
- Registration
- Login/Verify
Register Phase
A register interface would look something like this,
- When you create an account, your username (or email) and password get stored in a database in the form of a pair of strings, the password hash and the salt.
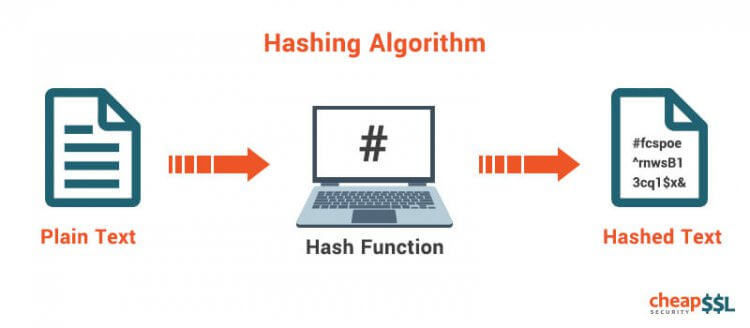
Hashing is the process of passing the password string into a one-way hashing function (SHA, bcrypt, etc.) which provides different unique values based on the input.
This is done to convert the plain-text password to unintelligible string.
In the event of a security breach, any compromised hashed passwords are not valuable to the bad actor.
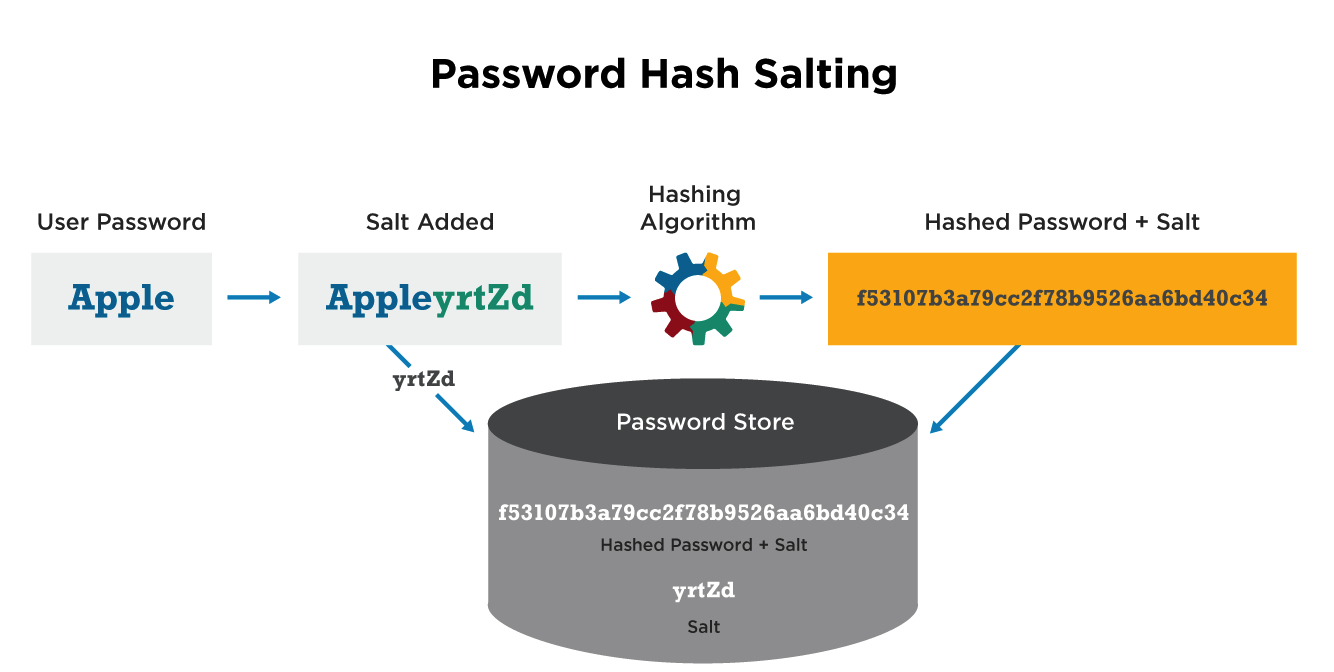
However, a common methodology which can be used to crack hashed strings is called rainbow table attack.
In this attack, the hashed passwords are checked against the rainbow table, containing a huge list of hashes along with their hashing function input (the plaintext)
If the password used is common and is in the rainbow table, the attacker can get access to the plain-text password.
This is where password salting comes into picture, we add a random string to the original password and then hash it, which ensures that the resulting hash would never be found in the rainbow table.
Login Phase
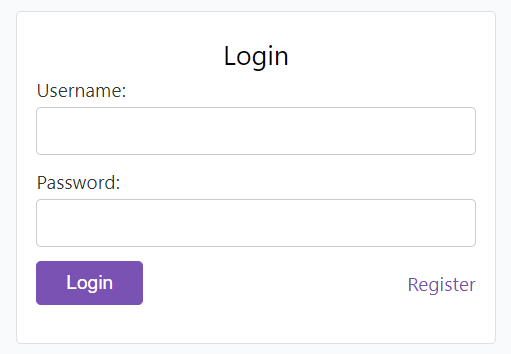
- When you try to log in after that, you’re prompted to enter your username and password
- Check if your username exists in the database
- Check the entered password by hashing it and comparing it against the hash in the database.
- If the above process succeed, you are not authenticated.
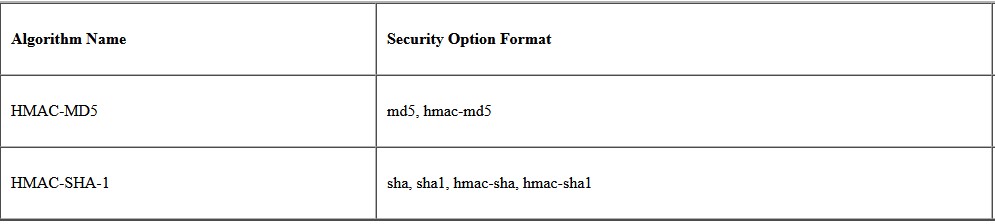
Authentication algorithms
Authentication algorithms produce an integrity checksum value or digest that is based on the data and a key. The authentication algorithm man pages describe the size of both the digest and key. The following table lists the authentication algorithms that are supported in the Solaris operating environment.
Types of Authentications:
- Password-based authentication
-
- Passwords are the most common methods of authentication. Passwords can be in the form of a string of letters, numbers, or special characters. To protect yourself you need to create strong passwords that include a combination of all possible options.
- Multi-factor authentication
-
- Multi-factor authentication (MFA) is an authentication method that requires two or more independent ways to identify a user. Examples include codes generated from the user’s smartphone, Captcha tests, fingerprints or facial recognition.
- Certificate-based authentication
-
- Certificate-based authentication technologies identify users, machines or devices by using digital certificates. A digital certificate is an electronic document based on the idea of a driver’s license or a passport.
- The certificate contains the digital identity of a user including a public key, and the digital signature of a certification authority. Digital certificates prove the ownership of a public key and issued only by a certification authority.
- Bio metric authentication
-
- Bio metrics authentication is a security process that relies on the unique biological characteristics of an individual. Here are key advantages of using bio metric authentication technologies
-
- Such as Facial recognition, fingerprint scanners, speech recognition and iris scanners.
- Token-based authentication
-
- Token-based authentication technologies enable users to enter their credentials once and receive a unique encrypted string of random characters in exchange. You can then use the token to access protected systems instead of entering your credentials all over again.
Implementation of basic authentication using HTTP security scheme
Basic authentication is a simple authentication scheme which is built into the HTTP protocol to send the request to the server.
- User has to login to the application by using a username and password
- Upon verifying the credentials, a base64 encoded string is generated for the username: password combination.

In this project, we will be creating a Web API with basic authentication and test it with Swagger UI.
Project structure:
- Controllers
-
- StudentController.cs
- Models
-
- Gender.cs
- StudentModel.cs
- Helpers
-
- BasicAuthenticationHandler.cs
Creating models
To represent binary gender properties, we use a gender enum.
Gender.cs
To represent a student entity, we create a class with Name, Age and Gender Properties.
StudentModel.cs
Now, we create a custom basic authentication handler which handles the following tasks,
- Fetch base64 string from the authentication header
- Split the string using the delimiter ‘:’ to get username and password
- Verifies the credential
Handling Authentication Header
BasicAuthenticationHandler.cs
Defining Controllers
In this project, we have a Student Controller with a single GET endpoint, which returns a list of Student model.
StudentController.cs
Defining Driver Class
As you can see, we have a student controller with a single endpoint and also notice the “Authorize” button on the top right part.
It is where we input our username and password for authentication.
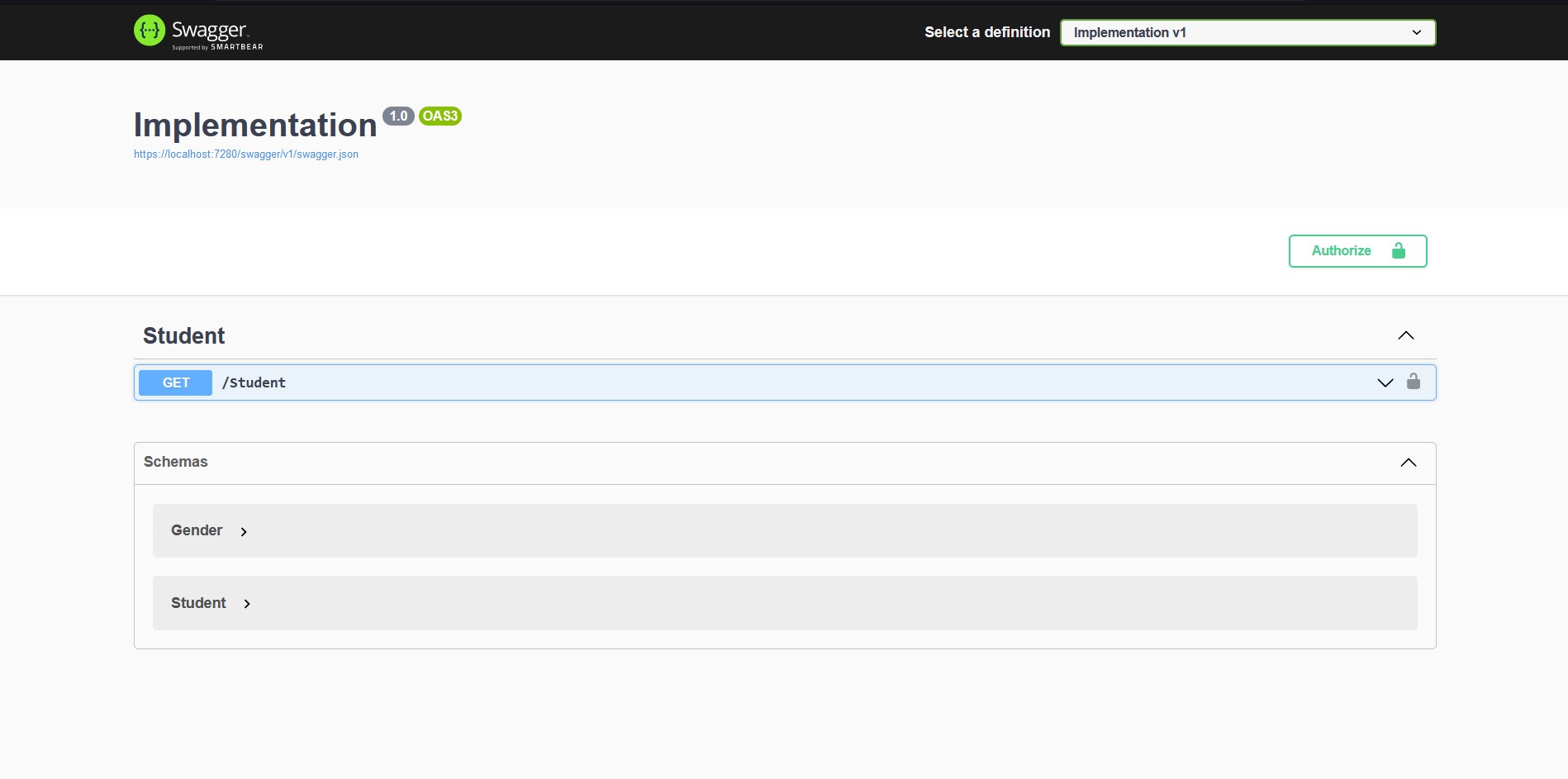
When I tried to hit the Get /Student endpoint, I get an Unauthorized error with 401 status code.

Now let us add the authentication headers by clicking on the authorize button and input some credentials.
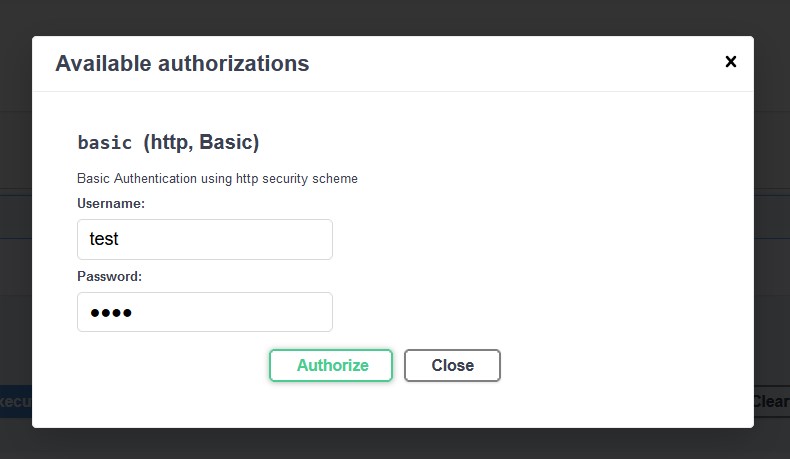
Notice, how the authorize button is now toggled on, so, when I try to hit the same endpoint again we get,
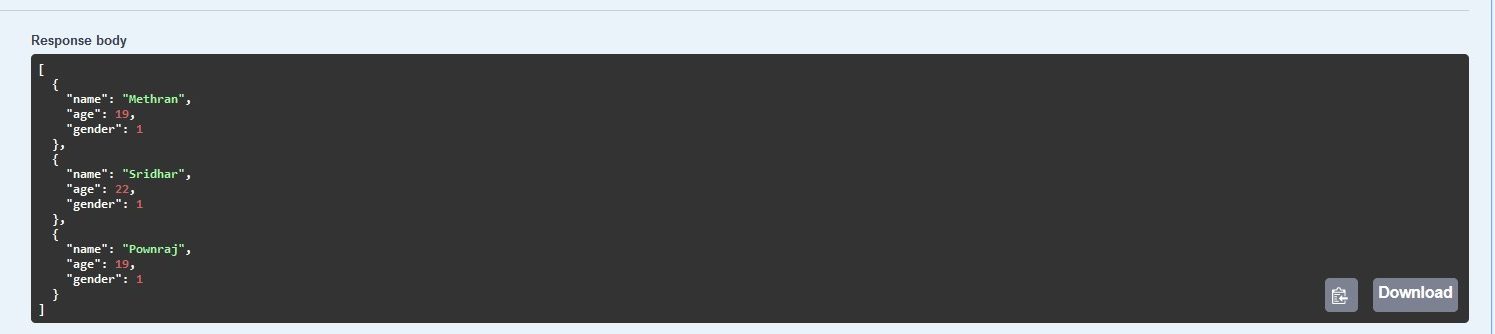
Conclusion
Implementing basic authentication in your web API project helps you to add additional security to your resources, makes data tamper and cyber attacks hard but not impossible.
So, implementing basic authentication does not provide guaranteed security, which is why we might need to use other authentication types such as the token based authentication.
To know more Token based authentication (JWT), refer this blog: https://www.techmeet360.com/blog/all-about-json-web-token-based-authentication/
GitHub Link: https://github.com/Mgs25/blog-code
Git is a free and open-source distributed version control system that can handle everything from tiny to extremely large projects quickly and efficiently. It was developed in 2005 by Linus Torvalds, creator of Linux Operating System.
To know more view: https://www.techmeet360.com/blog/global-information-tracker-git-workflow-and-terminologies/
