JSON WEB TOKEN
Authentication is basically the process of verifying who the user is. In order to authenticate the user , JWT (JSON Web Token) came into picture which is a token based authentication mechanism.
WHAT IS JWT ?
- JWT stands for JSON WEB TOKEN.
- It is the token based authentication mechanism to verify the owner of some JSON data. It’s an encoded, URL-safe string that can contain an unlimited amount of data (unlike a cookie) and is cryptographically signed.
WHY JWT ?
Session Based Authentication:
Let’s understand how session based authentication typically works,
- Initially before JWT came into picture, we predominantly used session based authentication.
- In this type of authentication mechanism, the server is responsible for the authentication and the client does not know what happens at the server side once after sending the request.
- The working of session based authentication mechanism was like , Whenever the user logins with their username and password(whenever the request is sent to the server) , the server creates the session for that user and store the session data in server memory.
- Server also creates the session ID for that particular user and stores the session ID as a cookie in the client browser.
- So then onwards whenever the same user makes request, that request is sent along with the session ID (cookie) and the server looks for the user with that particular Session ID and verifies them and returns the information as a response to the browser.
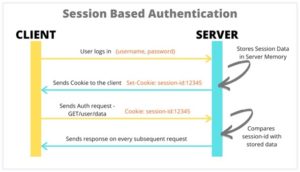
Problems faced using session-based authentication:
- So, here when multiple requests are made simultaneously, then the server will not be able to respond or process the request.
- So load balancing comes into picture.
- Once the server is loaded with multiple requests, it redirects you to the other server, so at that time, the user is asked to login again in order to create the session in server memory since its been redirected to the other server.
Token Based Authentication:
Let’s understand how JWT actually works,
- What actually happens here is,
Whenever the user logins with their username and password, the server creates an encrypted token in the form of JSON Web Token and sends that token to the client and then the client makes further requests with that Token
- So, when the server receives the request, server verifies JWT for that user and sends the appropriate response to the client.
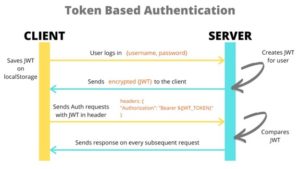
This is how the header is sent along with every request to the server :
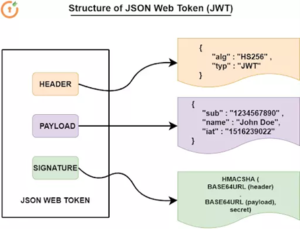
STRUCTURE OF JWT:
JSON Web Tokens consists of three parts concatenated by dots (.):
- Header
- Payload
- Signature
1.Header – ALGORTIHM AND TOKEN TYPE
- Contains the algorithm based on which it is going to sign.
- Type of the token (JWT)
2.Payload – DATA
- Contains the unique ID for that user, which is similar to session ID which is created in server in traditional approach
- Contains the data/claims of the user((might be name / username / email))
- Contains Issued at DATE(when the Token is created)
- Contains the expired date of that token
3.Signature – Based on the algorithm(RS256/HS256), it encodes both Header and payload using BASE64URLEncode and hashes it and stores it in Secret key.
Implementation of Authentication using JSON Web Token:
It is a web API project, where it contains of Register, Login, Create Token method Endpoint.
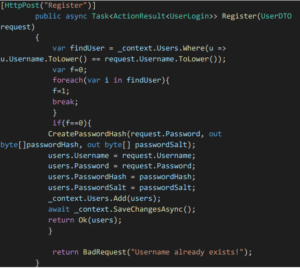
- Registration Endpoint:
- Once the user registers using their email and password, we will be checking whether the user is already registered. If registered we are setting the flag to 1 and we return a Bad Request. Else if Flag=0, then, we first create a password Hash and Salt and store the user in database.
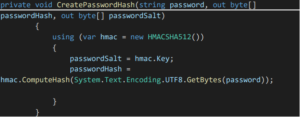
- Create Password Hash Method:
- In Create Password hash Method, we create the Password hash using HMAC SHA 512 algorithm
- Using Compute Hash method we compute the hash value for the specific byte array.
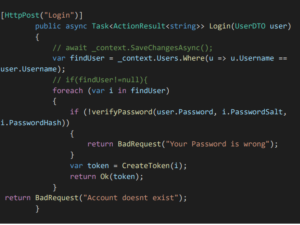
- Login Endpoint:
- Then when the user logins with the email and password, there is a method called verify password method wherein it will verify the password Hash stored in Database and the password hash created using the logged in password is same or not.
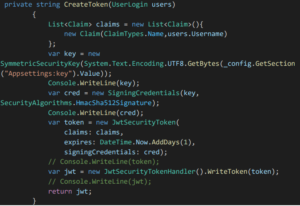
- If the password hash is same, then there is a method called create token where actually Json web token is created.
- In create token method, we will be mentioning the list of claims that the token should contain, and we will be returning a new instance of symmetric security key.
- Then we will create the token using Jwt Security Token class and return the token.
Now the user can send the further requests along with that token.
- Method for verifying the password during login:
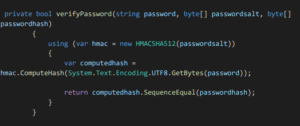
- Method for creating the Json web token:
Conclusion:
To conclude, JSON Web Tokens can prevent errors of inadequate authorization, allow simple and easy distribution of information flows between the servers. In order to make JWT more safe and secure, never transfer users sensitive information in tokens and use refresh token mechanism and limit the JWT lifespan
Here is the link to the implementation of Login Authentication using Json Web Token,
Github Link : https://github.com/DeebiKaaRaviSankar/Json-Web-Token
Git is a DevOps tool used for source code management. It is a free and open-source version control system used to handle small to very large projects efficiently.
To explore more about Global Information Tracker(GIT) , Refer : https://www.techmeet360.com/blog/global-information-tracker-git-workflow-and-terminologies/
